Vulnerability Detection Response (VDR)

VULNERABILITY DETECTION RESPONSE (VDR)

Unparalleled Continuous Vulnerability Detection and Response To Help Secure Your IT Environment
Even the best security strategy is defeated by the weakest link in your organization.
Secure IT™ Vulnerability Detection Response (VDR) powered by Qualys establishes the cyber security foundation that today’s hybrid, dynamic, and distributed IT environments require.
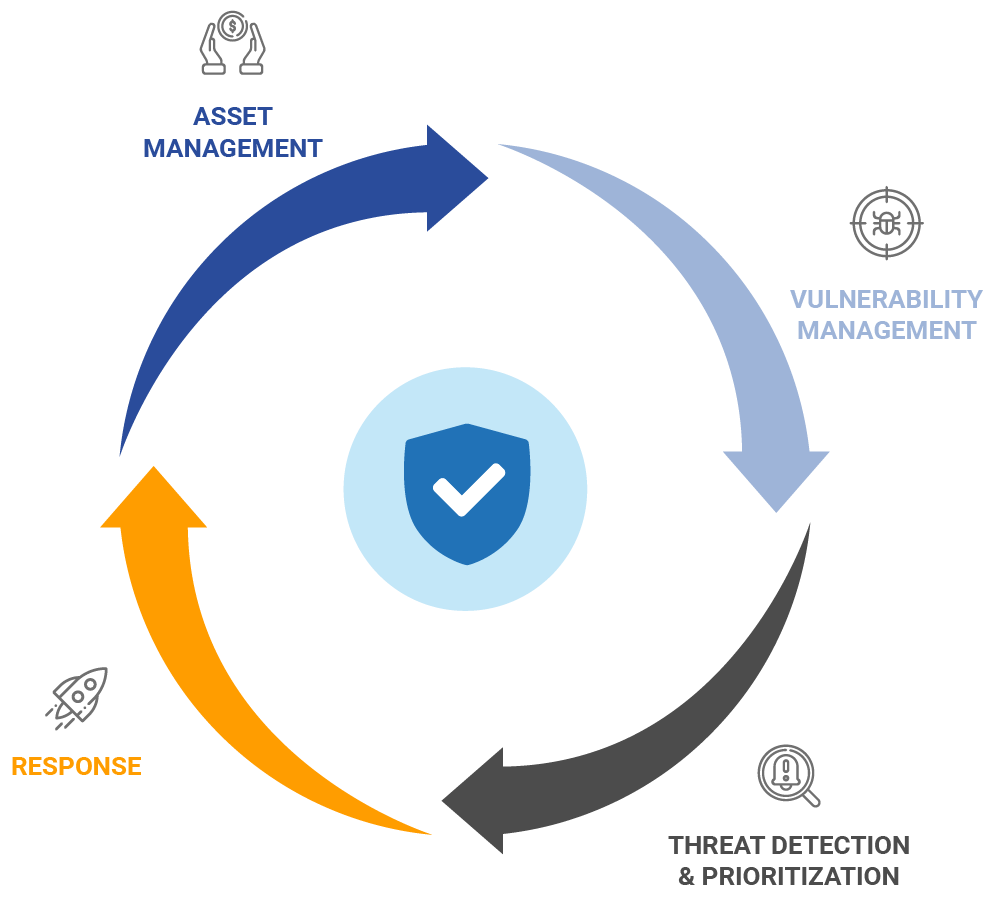
It is a continuously orchestrated workflow cycle, consisting of automated asset discovery, vulnerability management, threat prioritization, and optional remediation.
By adopting the Secure IT™ VDR lifecycle, organizations decrease their risk of compromise by effectively preventing breaches and quickly responding to threats.
Discover, assess, prioritize, and patch critical vulnerabilities in real-time and across your global hybrid-IT landscape — all from a single solution:
Identify all known and unknown assets on your global hybrid-IT.
Analyze vulnerabilities and misconfigurations with Six Sigma accuracy.
Detailed bi-monthly reporting to increase your security posture.
Inoculate your assets from ongoing threats with a detailed remediation plan.
Identify all known and unknown assets on your global hybrid-IT.
Analyze vulnerabilities and misconfigurations with Six Sigma accuracy.
Detailed bi-monthly reporting to increase your security posture.
Inoculate your assets from ongoing threats with a detailed remediation plan.
Threat Identification and Prioritization
Our Secure IT™ Vulnerability Detection Response solution uses threat identification using continuous threat intelligence to take control of the evolving threat landscape and to alert you when network anomalies are detected.


Patch Detection and Management
Our solution includes automatic correlation of vulnerabilities and patches which helps to decrease remediation response time. It searches for Common Vulnerabilities and Exposures (CVEs) to identify the latest superseding patches for rapid resolution.
Vulnerability Management
We offer continuous detection of software vulnerabilities with the most comprehensive signature database ranging across the widest category of assets. Our solution identifies vulnerabilities and misconfigurations in real-time across an entire hybrid environment.


Asset Discovery and Inventory
We conduct asset discovery, inventory, categorization, and normalization, of all known and unknown assets in real-time for easy review. This allows for a comprehensive, categorized global IT asset inventory that’s always up to date.
DEEP VISIBILITY, POWERFUL SCANNING
Everything visible, everything secure.
Secure IT™ VDR gives you a continuous, always-on analysis of your global hybrid-IT, security, and compliance posture, with visibility across all your IT assets, wherever they reside.
With automated, built-in threat prioritization and response capabilities, Secure IT™ VDR is a complete, end-to-end security solution.
Additional Benefits of Secure IT™ Vulnerability Detection Response
IT'S ALL IN THE CLOUD
![]()
ADVANCED THREAT MODELING
![]()
RAPID DEPLOYMENT
![]()
REDUCE TIME AND MONEY
![]()
Frequently Asked Questions
What type of reporting is provided with this solution?
We provide an in-depth report detailing the current state of the environment from a security perspective along with a prioritized list of vulnerabilities based on risk for rapid analysis of critical activities to be performed.
What are the supported OS/Technologies for this solution?
A list of supported OS/Technologies can be found through the following URL link :
How often will the remote vulnerability review be conducted?
We will present the found remote vulnerabilities with a remediation plan on a bi-monthly schedule. This will outline vulnerabilities in order of severity, to help provide direction in which items to address in order toto address detected vulnerabilities in the systems.
Related Solutions
Secure IT™ EDR
Delivers differentiated endpoint protection, endpoint detection and response.
Consult IT™
Professional services designed and implemented by a team of certified experts.
Secure IT™ User Defence
Tailored to empower your employees to become the first line of defence against cyber attacks.






