EXTENDED DETECTION
AND RESPONSE (XDR)

EXTENDED DETECTION AND RESPONSE (XDR)

Continuous Threat Visibility with Real-time Detection and Response to Protect Your Business
Secure IT™ XDR has been designed to meet stringent Cyber Insurance requirements, allowing your firm to obtain the best available coverages. XDR provides optimized threat detection and response that spans security and business tools. Contrary to legacy SIEM approaches and most current security analytics platforms, our XDR platform is built across multiple security disciplines, unifying your security services to give our security analysts deep visibility, real-time detection, and superior correlation, investigation, and response.
Holistic Protection Against Cyberattacks
The components that make our extended detection and response platform are comprised of global industry leaders in each security discipline.
Secure IT™ XDR enables organizations to dramatically reduce cyber-attack risks and create the confidence needed for one’s business. Extend beyond the endpoint with end-to-end enterprise visibility, protection, and response.
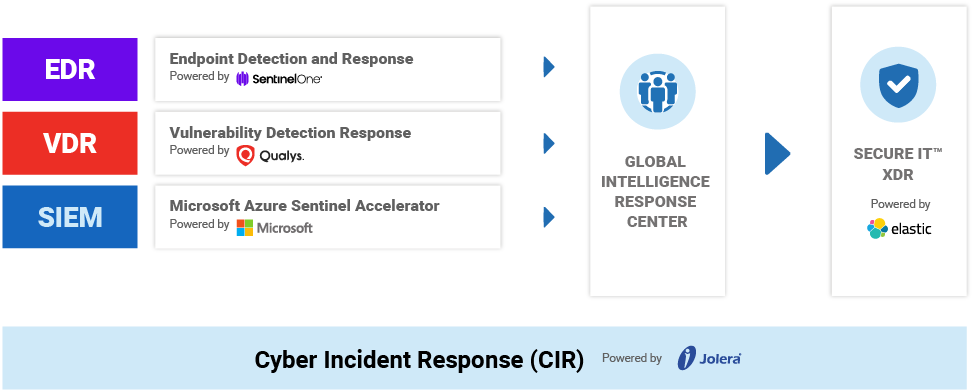
Our XDR Solution

Managed Detection & Response (MDR)
An integrated detection and response platform solution that stops modern attacks by integrating data from any source.

Endpoint Detection & Response (EDR)
An integrated endpoint security solution that combines real-time continuous monitoring and collection of endpoint data with rules-based automated response and analysis capabilities.

Vulnerability Detection and Response (VDR)
An integrated a risk-based vulnerability management solution that quantifies cyber risk.

Cyber Incident Response (CIR)
A no cost retainer version of our popular CIR service which provides rapid assistance in the event of a cyber-attack against an organization.

Azure Sentinel Enablement
A consulting service to help an organization to rapidly deploy Azure’s Sentinel platform providing SIEM and SOAR security services.
Threat Detection and Response
Our XDR solution provides an organization with true investigative oversight by cyber security experts who review threat data in real-time via our Global Threat Intelligence Center.

Advanced Adaptive AI + Machine Learning
Equip every endpoint and workload—no matter their location or connectivity—to respond intelligently against cyber threats with powerful AI and machine learning.
Integrated Real Time Threat Intelligence
With our XDR solution, you will be able to spot anomalies with machine learning and identify known threats with automated detection. In addition, you will also achieve rapid value with MITRE ATT&CK-aligned detections.


Threat Intelligence and Guided Remediation
Our XDR solution provides complete visibility of your cyberattack surface with threat intelligence to respond and stop threats with our global team of cyber threat hunters.
Stay in Compliance
While the insurance industry understands how best to insure cyber risk, premiums will continue to increase, and the amount of coverage offered may decrease or require greater cybersecurity investment by organizations that wish to establish and retain a policy. Our Secure IT™ Extended Detection and Response (XDR) solution was partially designed with this in mind. Our experience working with both advanced security technologies and cyber insurance firms have helped us to develop a product that meets and exceeds the requirements of most insurance companies and policies.
REGULATIONS
POLICIES
REQUIREMENTS

STANDARDS
RULES
Product Plans
We help you select the plan that best suits your needs
|
|
STANDARD
|
ADVANCED
|
Always-on monitoring (24/7/365) |
||
Live cyber security engineer support (24/7/365) |
||
Always-on threat hunting |
||
Always-on threat disruption and containment support |
||
Artificial Intelligence & Machine Learning to detect/stop threats in secs |
||
Automated rapid anomaly detection |
||
Scalable with no obligation to purchase hardware or software |
||
Detection of unknown attacks using behavioral analytics |
||
True rapid human-led investigations |
||
Public cloud and hybrid security threat protection models |
||
Detailed escalations with analysis and security recommendations |
||
Delivered through a single pane of glass via Jolera SaaS |
||
Business reviews and strategic continuous improvement planning |
||
Access to the 24/7 Global Intelligence and Response Center |
||
Single, integration and automated platform for complete visibility |
||
Cyber Incident Response – retainer free (CIR) * |
||
Vulnerability Detection and Response (VDR) |
 |
|
Endpoint Detection and Response (EDR) |
 |
|
Secure IT™ Azure Sentinel Accelerator platform |
 |
 |
*Conditions apply. Please speak with your account manager or read through the service agreement for more information.
Essentials
|
Essentials Plus |
|
Always-on monitoring (24/7/365) |
||
Live cyber security engineer support (24/7/365) |
||
Always-on threat hunting |
||
Always-on threat disruption and containment support |
||
Artificial Intelligence & Machine Learning to detect/stop threats in secs |
||
Automated rapid anomaly detection |
||
Scalable with no obligation to purchase hardware or software |
||
Detection of unknown attacks using behavioral analytics |
||
True rapid human-led investigations |
||
Public cloud and hybrid security threat protection models |
||
Detailed escalations with analysis and security recommendations |
||
Delivered through a single pane of glass via Jolera SaaS |
||
Business reviews and strategic continuous improvement planning |
||
Access to the 24/7 Global Intelligence and Response Center |
||
Single, integration and automated platform for complete visibility |
||
Cyber Incident Response – retainer free (CIR) * |
||
Vulnerability Detection and Response (VDR) |
 |
|
Endpoint Detection and Response (EDR) |
 |
|
Secure IT™ Azure Sentinel Accelerator platform |
 |
 |
Frequently Asked Questions
How is this solution different than a traditional antivirus?
Antivirus solutions have traditionally relied very heavily on something called ‘signature matching’ to determine threats to the device. AV software compares files against a known database of “bad” files.
Secure IT™ EDR includes monitoring and detection of threats, including those that may not be easily recognized or defined by standard antivirus. Secure IT™ EDR is behavior-based, so it can detect unknown threats based on a behavior that isn’t normal.
How does Secure IT™ EDR help me quickly respond to threats?
ActiveEDR intelligently automates EDR by providing Storyline context (shown in MITRE ATT&CK Phase 2 testing) and a full range of automated and manual remediation actions. Devices defend themselves autonomously by terminating and quarantining unauthorized processes and files in real-time. Devices also heal themselves with surgical, automated remediation and rollback to help reduce Mean Time to Remediate (MTTR). Threat hunters and incident responders can also use these functions to mark identified suspicious situations as threats for automatic, estate-wide remediation which greatly increases responder efficiency.
What types of USB devices can I control with Singularity Control?
Any kind! Administrators can create highly granular control for any type of USB device as defined by the USB standard. Policy can be defined by vendor ID, product ID, serial number or by class of device which includes things like audio, printers, mass storage, smart cards, video devices, USB-C devices, personal healthcare devices, and more.
What is meant by network control with location awareness?
Our solution offers native OS firewall control for Windows, Mac, and Linux. Your security policies may require different local OS firewall policies applied based on the device’s location. For example… perhaps a more restrictive policy is used outside the organization’s network vs. a more open policy inside the network. Administrators craft network location tests that help the endpoint automatically determine what network it’s connected to then applies the correct firewall policy accordingly.
What type of reporting is provided with this solution?
We provide an in-depth report detailing the current state of the environment from a security perspective along with a prioritized list of vulnerabilities based on risk for rapid analysis of critical activities to be performed.
What are the supported OS/Technologies for this solution?
A list of supported OS/Technologies can be found through the following URL link :
How often will the remote vulnerability review be conducted?
We will present the found remote vulnerabilities with a remediation plan on a bi-monthly schedule. This will outline vulnerabilities in order of severity, to help provide direction in which items to address in order toto address detected vulnerabilities in the systems.
How likely would it be that a small company like mine gets hit with cyberattack, where I would need to use Cyber Incident Response?
Ransomware has increased 443 percent over the last year during the pandemic so there is a good chance that even a small company would experience cyber security event.
What role does Jolera play with Cyber Incident Response?
All engagements are orchestrated through an Incident Response manager that is dedicated to your organization along with a team of incident responders.
Related Solutions
Secure IT™ Security Baseline Assessment
Comprehensive review of an environment for a baseline understanding of security posture.
Secure IT™ VDR
Decrease their risk of compromise by effectively preventing breaches and quickly responding to threats.
Secure IT™ EDR
Delivers differentiated endpoint protection, endpoint detection and response.






