demystifying series
What is Vulnerability Detection
and Response (VDR) ?
BREAKING DOWN THE BASICS
Vulnerability Detection and Response (VDR) is a cutting-edge cybersecurity solution that safeguards hybrid, dynamic, and distributed IT environments. VDR is a comprehensive security approach that identifies, manages, and responds to vulnerabilities to minimize the risk of cyber-attacks. MSPs should offer VDR solutions to provide their clients with comprehensive, proactive, and cost-effective security services, helping them differentiate themselves in a competitive market, improve client satisfaction, and grow their business.
What is a Vulnerability?
Understanding the nature of vulnerabilities in the context of cybersecurity is essential. As threats continue to evolve, partnering with a provider that stays current with these rapid changes is crucial to maintain a secure IT environment. Essentially, vulnerabilities are weaknesses or flaws in an IT system that, if discovered and exploited by a hacker, significantly increase the risk of a successful cyber-attack.
Vulnerabilities are unpredictable and can arise from poor design features or user errors over time. By collaborating with an expert provider who is well-versed in the ever-changing landscape of vulnerabilities, organizations can better protect their systems and data against potential threats. By doing so, businesses can focus on their core operations without the burden of worrying about potential cyber-attacks.
Burning Stats
Did you know?
%
of breaches involved stolen or weak passwords
What is VDR?
Vulnerability Detection and Response (VDR) is a cybersecurity approach that focuses on identifying, managing, and responding to vulnerabilities in an organization’s IT systems. VDR aims to minimize the risk of cyberattacks by continuously monitoring and analyzing the security posture of an organization’s software, hardware, and network infrastructure. By implementing a VDR solution, organizations can better understand and address their vulnerabilities, improve their security posture, and reduce the risk of cyber-attacks and data breaches. Key components of a VDR solution include:
Automated asset discovery
VDR solutions automatically identify and maintain an up-to-date inventory of an organization’s IT assets, ensuring that all devices and systems are accounted for and protected.
Vulnerability management
VDR continuously scans and assesses IT assets for known and potential vulnerabilities, providing a clear picture of the organization’s security status and helping prioritize remediation efforts.
Vulnerabilities prioritization
By integrating threat intelligence, VDR helps organizations prioritize vulnerabilities based on the likelihood and potential impact of an attack, allowing for more efficient allocation of resources and targeted security measures.
Real-time detection and response
VDR solutions emphasize continuous monitoring and rapid response to new vulnerabilities or active attacks, reducing the potential damage and improving overall security.
Integration with security tools
VDR often works in conjunction with other security tools, such as Security Information and Event Management (SIEM) systems and incident response platforms, to provide a comprehensive and streamlined approach to managing security incidents and vulnerabilities.
How does VDR work?
A VDR solution continuously establishes a security foundation for hybrid, dynamic, and distributed IT environments by utilizing the latest threat intelligence available. This process operates in a seamless, orchestrated workflow cycle, which includes automated asset discovery, vulnerability management, threat prioritization, and optional remediation. With VDR, your organization gains real-time solutions that can reduce the risk of compromise, prevent data breaches, rapidly respond to threats such as Zero-Day attacks, and minimize the overall attack surface.
What’s new with VDR?
Recent advancements in VDR have improved its ability to address the ever-changing cybersecurity landscape. These advancements have made VDR more effective and versatile, helping organizations stay ahead of emerging threats and maintain a robust cybersecurity posture. Some notable developments include:
Threat intelligence integration
VDR now incorporates threat intelligence to better understand the likelihood and potential impact of attacks, enabling more effective prioritization of security efforts.
Automated asset discovery
VDR solutions have improved their capabilities to automatically maintain an up-to-date inventory of IT assets, ensuring accurate vulnerability detection and protection.
monitoring and real-time response
VDR has evolved to emphasize rapid detection and response to new vulnerabilities or active attacks, helping reduce potential damage and strengthen overall security.
Integration with security tools
VDR increasingly collaborates with other security tools, such as SIEM systems and incident response platforms, for a more cohesive and efficient security management approach.
AI and machine-learning
VDR leverages artificial intelligence and machine learning technologies to enhance detection accuracy, automate remediation processes, and enable predictive analytics, which allows for more proactive security measures.
What is a Zero-Day attack and how does it impact cybersecurity?
A zero-day attack is a type of cyberattack where hackers take advantage of a previously unknown weakness in computer software or hardware. These weaknesses, or vulnerabilities, haven’t been discovered by the software creators or security experts yet, which means there’s no fix available. The term “zero-day” comes from the fact that the developers have had zero days to address the issue, leaving systems vulnerable. To protect against zero-day attacks, organizations should take a proactive approach to cybersecurity, including keeping software up to date, closely monitoring systems, assessing potential vulnerabilities, staying informed about threats, training employees, and using advanced security tools that can detect and respond to new and unknown threats. Zero-day attacks can cause significant problems for cybersecurity for several reasons:
Unknown weaknesses
Since these attacks target unknown vulnerabilities, traditional security measures like antivirus software or firewalls might not be effective in stopping them.
Quick damage
Hackers can take advantage of zero-day vulnerabilities very quickly, often causing serious harm before a solution is developed and distributed.
High-value targets
Zero-day attacks often target important organizations, like government agencies or large companies, where the potential for damage and disruption is significant.
Sneaky attacks
Zero-day attacks can be part of more complex cyberattacks, where skilled hackers infiltrate a target and maintain access to the system for a long time, often to steal sensitive data.
Expensive
Dealing with zero-day attacks can be costly and require a lot of effort, as organizations must identify the problem, create a solution, and apply the fix to affected systems.
How can VDR improve overall security?
With VDR, organizations can reduce their attack surface for hackers by identifying and addressing vulnerabilities before they can be exploited. This leads to improved security and peace of mind for end users, who can work each day without fear of a data breach or security hack. Vulnerability Detection and Response (VDR) is a comprehensive security solution that helps organizations improve their security posture by:
1.
Providing ongoing identification and evaluation of vulnerabilities
2.
Treating or remediating vulnerabilities before they can be exploited
3.
Reducing the attack surface for hackers
4.
Offering insights into the overall threat landscape
5.
Enabling proactive measures against emerging threats
6.
Monitoring and prioritizing threats on a continuous basis
7.
Providing automated correlation of vulnerabilities and patches to decrease remediation response time
8.
Delivering real-time asset discovery, inventory, and categorization of known and unknown assets regardless of their location.
Enhancing Endpoint Detection and Response with VDR
Vulnerability Detection and Response (VDR) and Endpoint Detection and Response (EDR) can work together to provide comprehensive protection against cyber threats. While EDR focuses on detecting and responding to threats on endpoints, VDR identifies vulnerabilities in the IT environment and prioritizes them for remediation to reduce the risk of successful attacks. Overall, by combining VDR with EDR, organizations can benefit from a more comprehensive and effective security strategy that helps reduce the risk of successful cyber attacks. By implementing VDR alongside EDR, organizations can benefit from:

Increased visibility
VDR provides organizations with a comprehensive view of vulnerabilities across the entire IT environment, including endpoints. This visibility enables organizations to quickly identify potential security weaknesses and prioritize remediation efforts.

Reduced attack surface
VDR helps organizations reduce their attack surface by identifying and addressing vulnerabilities before they can be exploited by attackers. This complements the proactive threat detection capabilities of EDR and helps organizations better defend against both known and unknown threats.

Improved response times
VDR’s automatic correlation of vulnerabilities and patches helps organizations reduce the time it takes to remediate vulnerabilities, which can be critical in preventing successful attacks. This complements the rapid incident response capabilities of EDR, enabling organizations to more effectively contain and mitigate the impact of attacks.
Burning Stats
Did you know?
%
of incidents have web application attacks as the leading cause
How do you get started with VDR?
Collaborating with a reputable Managed Service Provider (MSP) in your local area can grant any organization, irrespective of size, access to a VDR solution that caters to their distinct needs and objectives. Entrusting your MSP with the responsibility of identifying a VDR solution that aligns with your specific requirements can be a smart investment for your organization.
If your current MSP does not offer VDR solutions, it’s crucial to investigate the reasons behind it and explore alternative options. By conducting thorough research and soliciting advice from industry experts, you can gain valuable insights into available security options and make informed decisions that will help safeguard your organization’s assets.
What makes Jolera’s Secure IT™ Vulnerability Detection and Response (VDR) different?
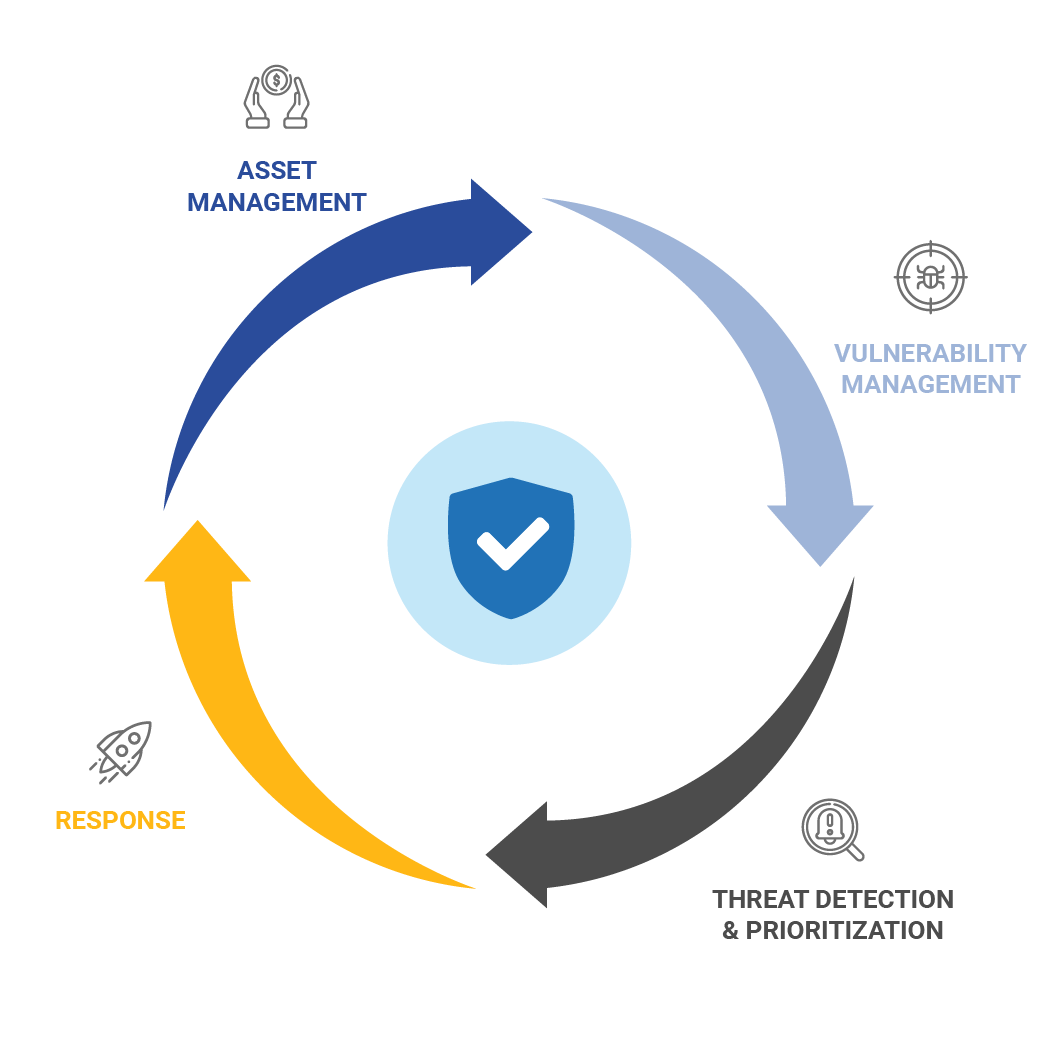
Jolera’s Secure IT™ Vulnerability Detection and Response (VDR), powered by Qualys, offers a cutting-edge solution to safeguard your hybrid, dynamic, and distributed IT environments.
Our continuously orchestrated workflow cycle combines automated asset discovery, vulnerability management, threat prioritization, and optional remediation to provide comprehensive protection.
Our Global Intelligence Response Center (GIRC) includes a team of expert threat hunters who continuously monitor vulnerabilities in real-time, helping counter and prevent threats.
As a fully managed service, Secure IT™ VDR includes everything you need to protect your environment from vulnerabilities of any kind.
Secure IT™ VDR enables organizations to stay ahead of emerging threats and maintain a robust cybersecurity posture while benefiting from the expertise and real-time vigilance of our GIRC team.
Key features of our Secure IT™ VDR solution include:

Prioritized remediation
Identification of vulnerabilities with the most significant impact on your risk exposure, providing prioritized remediation recommendations.
Deep visibility and insight
Comprehensive insight into your expanding IT systems, including on-premises, remote, and cloud-based assets.
Real-time asset management
Asset discovery, inventory, categorization, and normalization of all known and unknown assets in real-time for easy review.
Detailed security reporting
In-depth reports that help enhance your organization’s security posture by identifying vulnerabilities most likely to be exploited by threat actors.
Policy and compliance
Satisfy regulatory requirements for various mandates, such as PCI, NIST, CIS, or general cyber insurance, with optional policy and compliance scanning.
Burning Stats
Did you know?
are the average days to detect and contain a data breach
Why should MSPs offer VDR?
MSPs should offer VDR solutions to their customers as it will offer numerous benefits such as rapidly reducing the attack surface of any sized organization. VDR solutions also deliver automated asset discovery, improved vulnerability management and threat prioritization and remediation.
Offering VDR as a security solution enables MSPs to provide comprehensive, proactive, and cost-effective security services to their clients. This helps MSPs differentiate themselves in a competitive market, improve client satisfaction, and ultimately grow their business.
Conclusion
Jolera’s Secure IT™ VDR, powered by Qualys, offers a comprehensive solution to protect diverse IT environments. Key features such as prioritized remediation, deep visibility, real-time asset management, and detailed reporting help organizations stay ahead of threats and maintain a robust cybersecurity posture. With the dedicated support of our GIRC team of expert threat hunters, Secure IT™ VDR enables organizations to take control of their cybersecurity, reduce risk, and safeguard their digital assets.

