


How to eliminate high-risk security attacks in real-time
The trick to eliminating high-risk security attacks is to properly identify vulnerabilities before cybercriminals can begin to exploit them. Most organizations begin to take action when a security attack is either imminent or has actually occurred. They probably...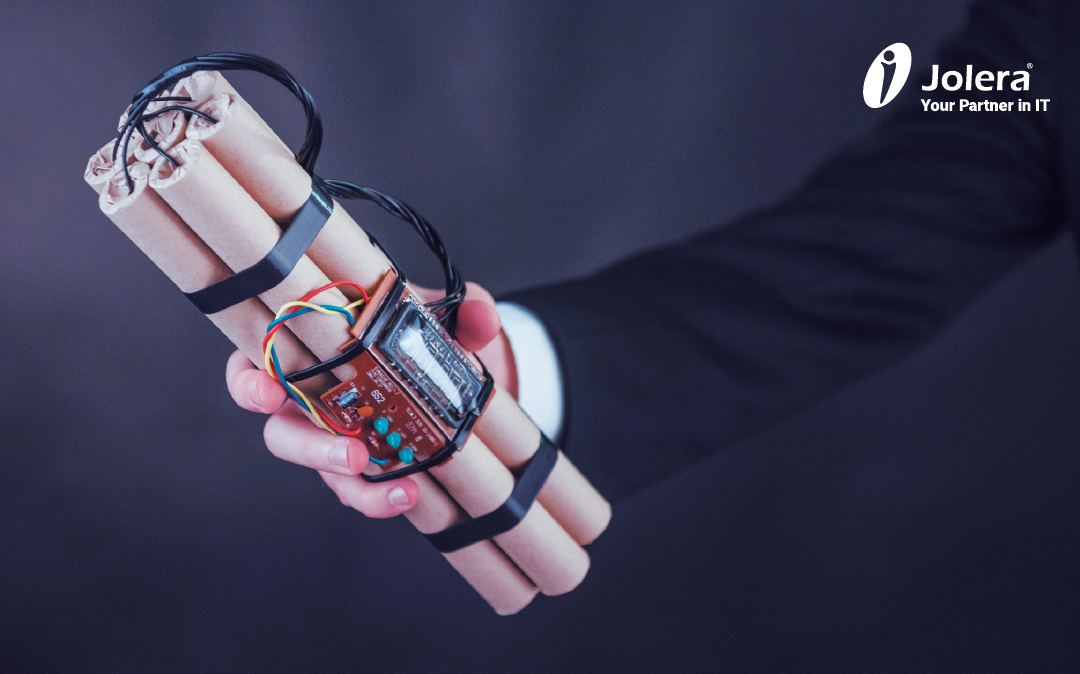
Security Threats Are Closer than they Appear
Protect Your Organization from Threats and Hackers with a Security Baseline Assessment When you look at your car’s side mirrors, the sticker on the mirror will say “Objects in the mirror are closer than they appear.” This warning message is used to help drivers...
Security Breach! A ticking time bomb for your business
Tick. Tick. Tick. That’s the sound of your organization getting hit with a significant breach. The coming impact of the breach depends on how quickly your organization can mitigate damage and find a solution. Acting within the first 48-hours after a breach is critical...
The value of a Security Operations Center for MSPs
When you work inside of a Security Operations Center (or SOC for short), the day never ends. It’s demanding and often a seven-days-a-week job, according to Sagar Vyas, the Global Cybersecurity Evangelist for Jolera Inc. Working inside a SOC is a fast-paced environment...
You can’t just Google your Cyber Security
The ChannelNext Central conference recently concluded, leaving the industry buzzing with ways to boost their Managed Service Providers (MSP) security offerings and intelligences. Claudio Damaso, associate partner, cloud, and security for Hillsburgh, Ont. based...
The biggest Phishing Scams of the last decade
October is Cybersecurity Awareness Month, so it’s almost mandatory to explore one of the biggest cyber threats known to date. Phishing scams are amongst the greatest cyber security threats that businesses and organizations face today. 75% of organizations around...
ChannelNext East show gets back to In-Person events
The ChannelNext East conference in Montreal was my first in-person event since January of 2020 and it hosted local channel partners and MSPs from the area as well as several more who live-streamed the show. The one-day event was held at the Riverside Event Venue in...
Getting the Most from your Managed Service Provider
The decision to outsource some or most IT operations to an external MSP (Managed Service Provider) is one that could directly benefit your entire company. MSPs can bring value by allowing your company to focus on what it does best without sacrificing time on managing...





